Code Robo
- Generate Java Code To Parse XML
- Generate Java Code To Parse JSON
- XSLT(XSL) Code Generator
- XSLT To Produce JSON(*New)
- REST API/Service Code End To End (Spring boot/MVC)(*New)
- XML To POJO(Java Bean)
- XML To JavaBean
- XML To XSD (XSD From XML)
- XML To XPath (Gen XPath)
- XSD To XML(XML From XSD)
- XSD To Java Bean(POJO)(*New)
- JSON To Java Bean
- JSON To POJO(Java Bean)
- JSON To JavaScript
- JSON To Angular Code(*New)
- JSON To AngularJS Code
- JSON Path Generator
- JSON To JSON Schema(*New)
- JSON Schema To JSON(*New)
- Generate DAO Code(SQL To Java)
- Generate JUnit TestCase(*New)
Formatter
Comparator
Tester
Merger
Converter
- Base64 To Text / Text To Base64
- Base64 To Image (*New)
- CSV To XML
- CSV To JSON
- JSON To YAML
- JSON To XML
- JSON To Text
- JSON To MappingDoc
- JSON To Excel
- JSON To Property
- Property To YAML
- Property To JSON
- SQL To JSON / XML (*New)
- XML To Excel
- Text To HTML
- XML To JSON
- XML To Mapping Doc
- XML To Template
- XML To Text
- YAML To Property
- YAML To JSON
Utility
Java Code Complience
Validator
EncoderDecoder
Virtual Service
java.io.IOException: Key exchange was not finished, connection is closed. |
Talk to EasyAssistant |
Solve 'java.io.IOException: Key exchange was not finished, connection is closed' exception and 'java.io.IOException: Cannot negotiate, proposals do not match.' exception with REHL 9 instance in AWS ..
This page tells you how to solve the "java.io.IOException: Key exchange was not finished, connection is closed" exception or "Caused by: java.io.IOException: Cannot negotiate, proposals do not match." issue when user is trying to connect redhat linux (RHEL) 9 from a java clinet program over SSH using ganymed library/jar and authenticated by key .If you trying to connect Red Hat Linux (RHEL) centos 9 over SSH using ganymed-ssh-2 library and getting following exception, you can solve it by following change..
Key exchange was not finished, connection is closed with ganymed-ssh-2 and Cisco Confd
Exception:
Exception in thread "main" java.io.IOException: Key exchange was not finished, connection is closed. at ch.ethz.ssh2.transport.KexManager.getOrWaitForConnectionInfo(KexManager.java:76) at ch.ethz.ssh2.transport.TransportManager.getConnectionInfo(TransportManager.java:169) at ch.ethz.ssh2.Connection.connect(Connection.java:759) at ch.ethz.ssh2.Connection.connect(Connection.java:628) at comz.ConnectRemoteAndExecute.connectAndExecute(ConnectRemoteAndExecute.java:33) at comz.ConnectRemoteAndExecute.main(ConnectRemoteAndExecute.java:16) Caused by: java.io.IOException: Cannot negotiate, proposals do not match. at ch.ethz.ssh2.transport.ClientKexManager.handleMessage(ClientKexManager.java:123) at ch.ethz.ssh2.transport.TransportManager.receiveLoop(TransportManager.java:572) at ch.ethz.ssh2.transport.TransportManager$1.run(TransportManager.java:261) at java.base/java.lang.Thread.run(Thread.java:833)
Solution:
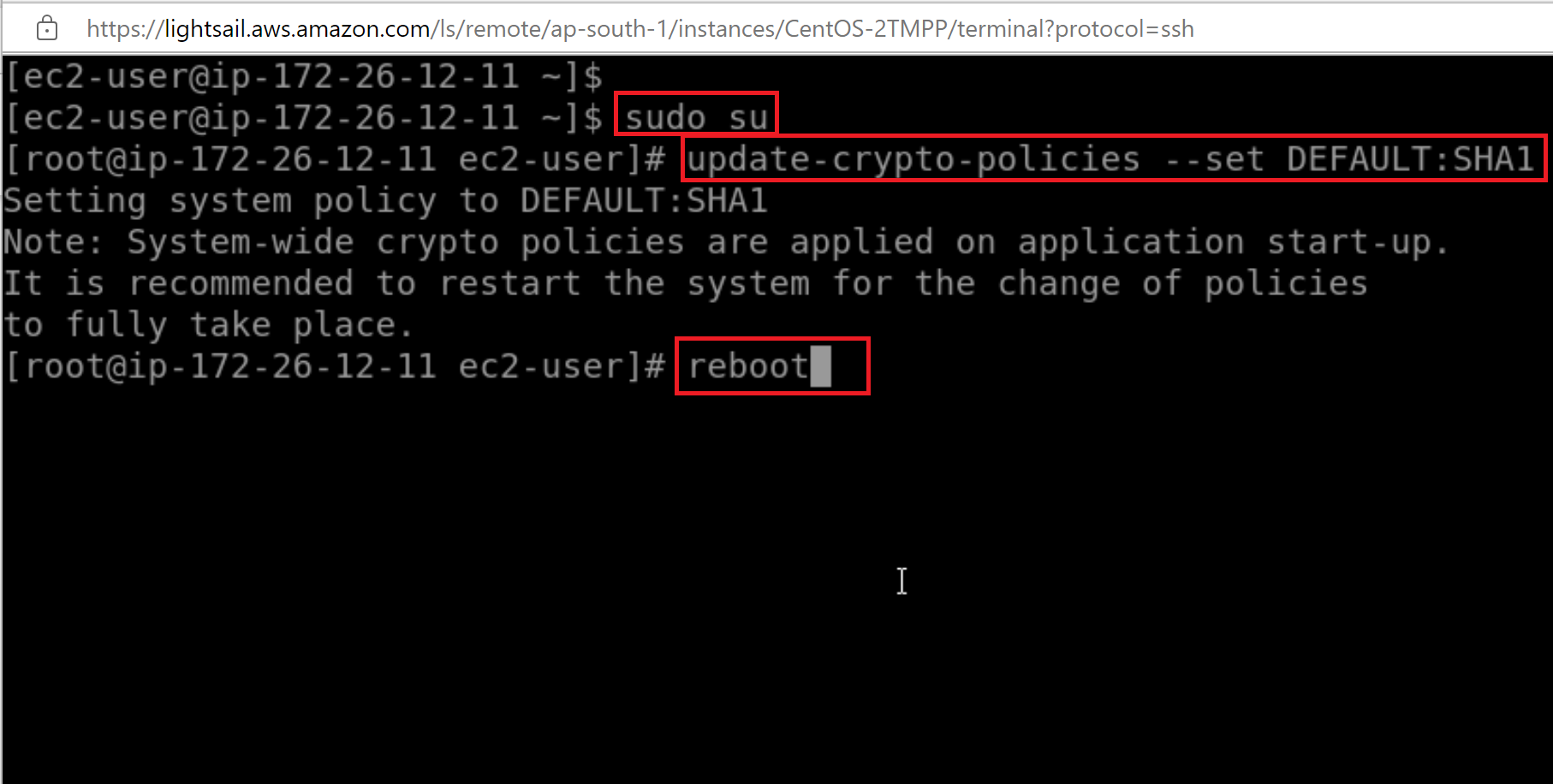
In Redhat Linux 9 (RHEL) SHA1 has been depricated. As a work around this DEFAULT:SHA1 crypto policy can be set forcefully by executing the command : "update-crypto-policies --set DEFAULT:SHA1" .
By setting a crypto policy of DEFAULT:SHA1 to re-enable SHA-1 security will be lower down but as temporarily solution it may be used.
1. Apply the SHA1 subpolicy to the DEFAULT cryptographic policy:
command : update-crypto-policies --set DEFAULT:SHA1
2. Reboot the system:
command : reboot
Screenshot is given below:
| Post Your Comment: |